Brilliance in the Basics – 5: Data Backups and Redundancy
Explore the vital role of regular data backups in protecting your information, making loss or theft a minor inconvenience rather than a major catastrophe.
Brilliance in the Basics – 2: Diverse Passwords
Delve into the critical necessity of diverse passwords, your first line of defense against cyber threats, and learn how to manage them effectively.
Brilliance in the Basics – 3: Software Updates
Uncover the importance of software updates and how they arm your devices with crucial protection against cyberattacks.
Brilliance in the Basics – 1: Two-Factor Authentication
Discover the power of an additional security layer with 2-Factor Authentication, making your accounts tougher to compromise and your digital world safer.
Brilliance in the Basics – An Essential Cybersecurity Guide for Everyone
Dive into our 'Brilliance in the Basics' series, where we simplify the top five cybersecurity practices everyone should follow, making digital safety achievable and understandable.
iOS 16.5: 39 Security Vulnerabilities Patched
Discover the crucial role of iOS 16.5 in protecting your iPhone against 39 security vulnerabilities, three of which are under active exploitation.
Why You Need a Password Manager: A Cybersecurity Must-Have
Password managers, as secure digital tools, actively store all your passwords in an encrypted vault, offering both convenience and enhanced security for your online presence.
Defend Your Mac: Tackling MacStealer & Atomic macOS Malware
MacStealer and Atomic macOS Stealer malware, these two malware families, are recent discoveries that specifically target macOS systems, stealing passwords, credit card information, and various files from infected Macs.
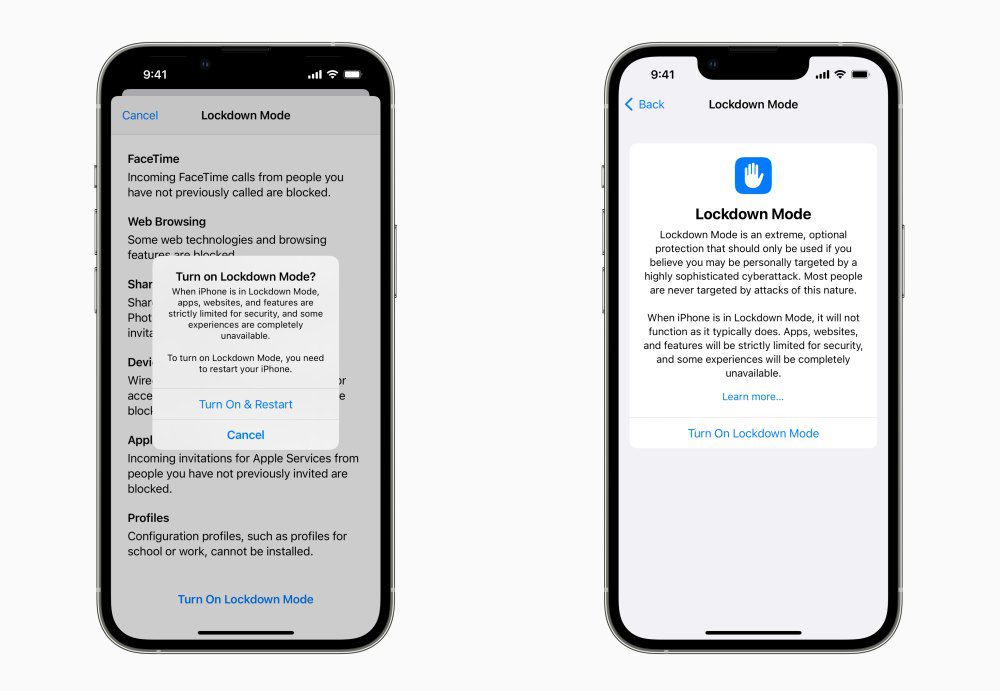
Keep Your iPhone Safe with Lockdown Mode
Lockdown Mode on iPhones provides an extra layer of security by blocking potential attack vectors, keeping your device safer. Enable it through your iPhone's Privacy & Security settings and follow additional security tips to protect your personal information.
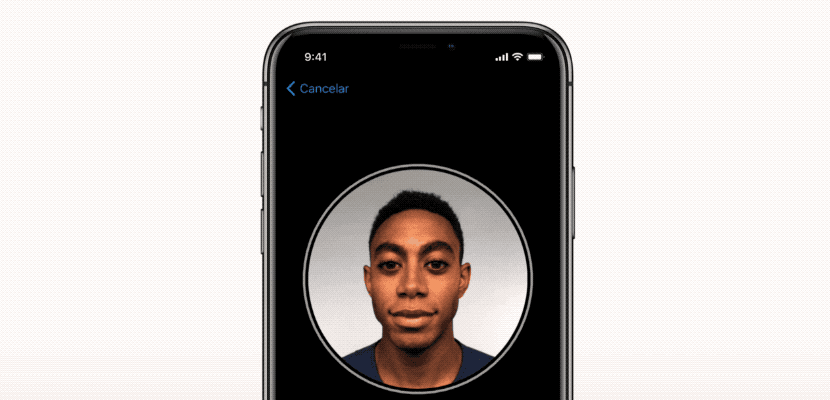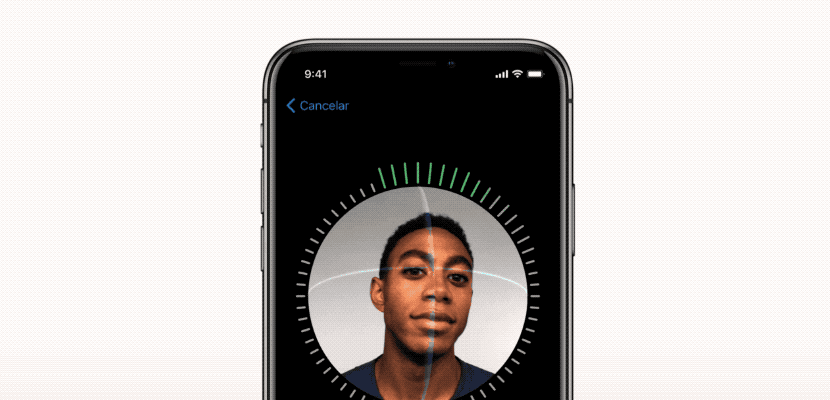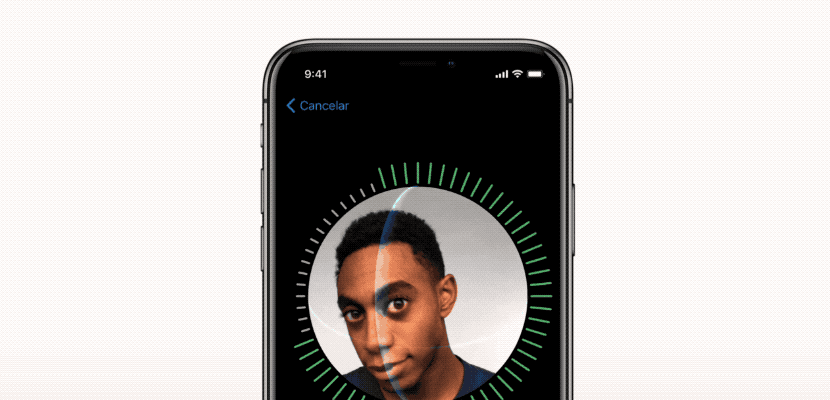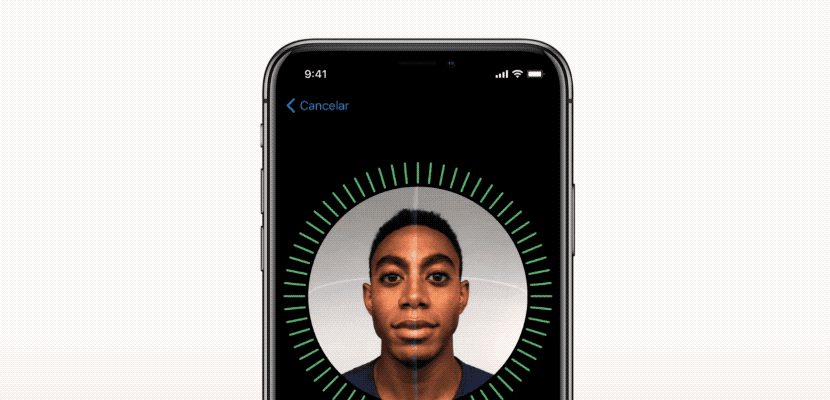
Protect Your iPhone with Face ID
Unlock your iPhone securely with Face ID! This facial recognition technology provides an additional layer of protection against phone theft and cybercrime, especially in public spaces. Face ID is more secure than a passcode and more convenient, as it recognizes you even with accessories like hats or glasses.
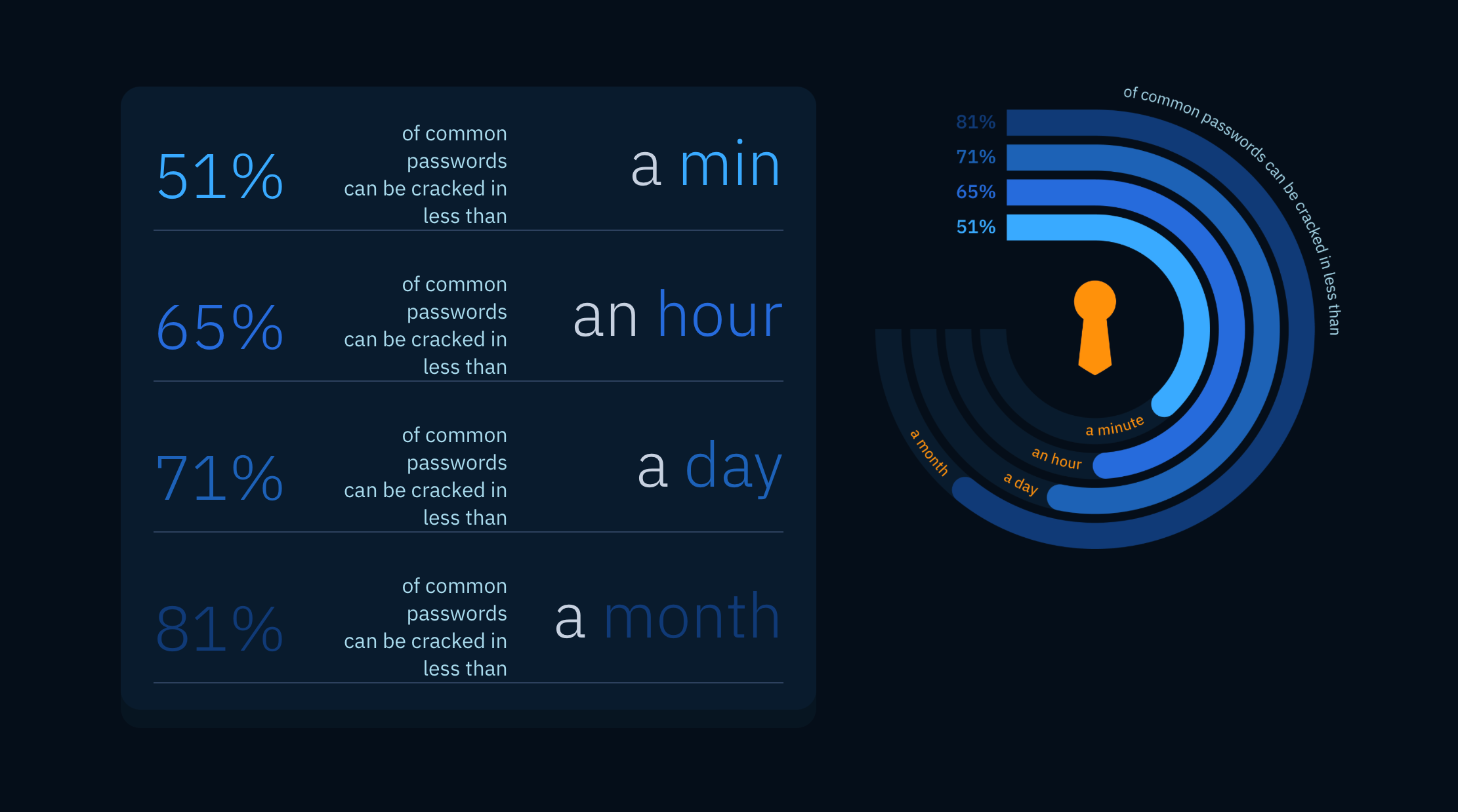
AI vs. Your Passwords: How to Safeguard Your Online Accounts
A recent study revealed that an AI-based password-cracking tool called PassGAN managed to compromise an alarming 51% of passwords in under a minute.
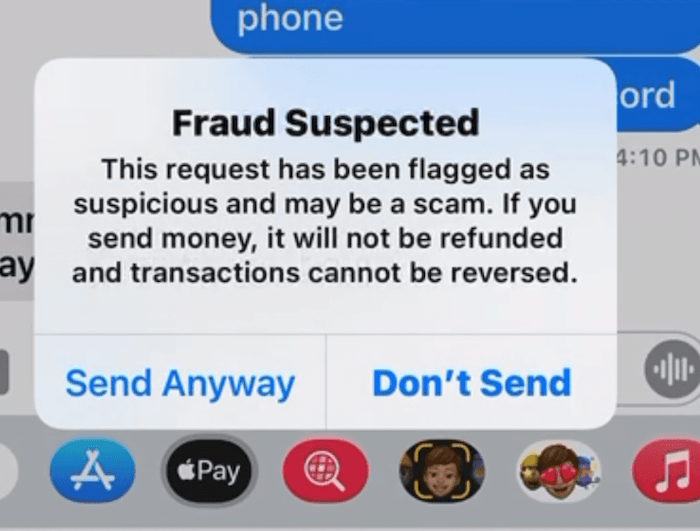
Apple Cash Scams
Apple Cash has made it incredibly convenient to send and receive money instantly. However, it's important to be cautious and understand how to recognize common scams to keep your financial transactions secure.
iPhone Users: Be Aware of Juice Jacking
"Juice jacking" refers to the practice of hacking into phones through USB cables at public charging stations to steal data or infect devices with malware.
Rorschach Ransomware: A Sophisticated Threat on the Horizon
Meet Rorschach: The game-changing, lightning-fast ransomware. Encrypting 220,000 files in just 4.5 minutes, victims have less time than ever to defend their systems. Discover its unique characteristics and learn how to protect your data from this sophisticated threat.
The Asymmetrical Impact of AI on Cybersecurity
In this post, we explore how AI is reshaping the world of cybersecurity, the potential asymmetry in its deployment, and the implications for organizations and individuals alike.
Pinduoduo: Malware in a Mainstream App
Pinduoduo, a popular shopping app in China with over 750 million users per month, has been found to contain malware capable of bypassing phone security, monitoring activities on other apps, reading private messages, and altering settings.